Encryption is the method by which plaintext or any other type of data is converted from a readable form to an encoded version that can only be decoded by another entity if they have access to a decryption key. Encryption is one of the most important methods for providing data security, especially for end-to-end protection of data transmitted across networks.
Encryption is widely used on the internet to protect user information being sent between a browser and a server, including passwords, payment information and other personal information that should be considered private. Organizations and individuals also commonly use encryption to protect sensitive data stored on computers, servers and mobile devices like phones or tablets.
Types of Modern Encryption
All the fancy encryption algorithm that we have talked about earlier are mostly used for two different types of encryption:
- Symmetric key algorithms use related or identical encryption keys for both encryption and decryption.
- Asymmetric key algorithms use different keys for encryption and decryption—this is usually referred to as Public-key Cryptography.
Symmetric Key Encryption
To explain this concept, we’ll use the postal service metaphor described in Wikipedia to understand how symmetric key algorithms work.
Alice puts her secret message in a box and locks the box using a padlock to which she has a key. She then sends the box to Bob through regular mail. When Bob receives the box, he uses an identical copy of Alice’s key (which he has somehow obtained previously, maybe by a face-to-face meeting) to open the box and read the message. Bob can then use the same padlock to send his secret reply.
Symmetric-key algorithms can be divided into stream ciphers and block ciphers—stream ciphers encrypt the bits of the message one at a time, and block ciphers take a number of bits, often in blocks of 64 bits at a time, and encrypt them as a single unit. There’s a lot of different algorithms you can choose from—the more popular and well-respected symmetric algorithms include Twofish, Serpent, AES (Rijndael), Blowfish, CAST5, RC4, TDES, and IDEA.
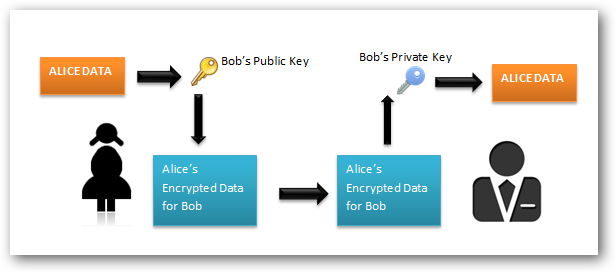
Asymmetric Encryption
In an asymmetric key system, Bob and Alice have separate padlocks, instead of the single padlock with multiple keys from the symmetric example. Note: this is, of course, a greatly oversimplified example of how it really works, which is much more complicated, but you’ll get a general idea.
First, Alice asks Bob to send his open padlock to her through regular mail, keeping his key to himself. When Alice receives it she uses it to lock a box containing her message and sends the locked box to Bob. Bob can then unlock the box with his key and read the message from Alice. To reply, Bob must similarly get Alice’s open padlock to lock the box before sending it back to her.
The critical advantage in an asymmetric key system is that Bob and Alice never need to send a copy of their keys to each other. This prevents a third party (perhaps, in the example, a corrupt postal worker) from copying a key while it is in transit, allowing said third party to spy on all future messages sent between Alice and Bob. In addition, if Bob were careless and allowed someone else to copy his key, Alice’s messages to Bob would be compromised, but Alice’s messages to other people would remain secret since the other people would be providing different padlocks for Alice to use.
Asymmetric encryption uses different keys for encryption and decryption. The message recipient creates a private key and a public key. The public key is distributed among the message senders and they use the public key to encrypt the message. The recipient uses their private key any encrypted messages that have been encrypted using the recipient’s public key.
There’s one major benefit to doing encryption this way compare to symmetric encryption. We never need to send anything secret (like our encryption key or password) over an insecure channel. Your public key goes out to the world—it’s no secret and it doesn’t need to be. Your private key can stay snug and cozy on your personal computer, where you generated it—it never has to be e-mailed anywhere, or read by attackers.
How Encryption is Used

Encryption was almost exclusively used only by governments and large enterprises until the late 1970s when the Diffie-Hellman key exchange and RSA algorithms were first published — and the first personal computers were introduced. By the mid-1990s, both public key and private key encryption were being routinely deployed in web browsers and servers to protect sensitive data.
Encryption is now an important part of many products and services, used in the commercial and consumer realms to protect data both while it is in transit and while it is stored, such as on a hard drive, smartphone or flash drive (data at rest).
Devices like modems, set-top boxes, smartcards and SIM cards all use encryption or rely on protocols like SSH, S/MIME, and SSL/TLS to encrypt sensitive data. Encryption is used to protect data in transit sent from all sorts of devices across all sorts of networks, not just the internet; every time someone uses an ATM or buys something online with a smartphone, makes a mobile phone call or presses a key fob to unlock a car, encryption is used to protect the information being relayed. Digital rights management systems, which prevent unauthorized use or reproduction of copyrighted material, are yet another example of encryption protecting data.
It’s a good idea to access sites utilizing SSL when
- You store or send sensitive data online – If you use the Internet to carry out tasks such as filing your taxes, make purchases, renew your driver’s license, or conduct any other personal business, visiting sites utilizing SSL is a wise idea.
- Your work requires it – Your workplace may have encryption protocols, or it may be subject to regulations that require encryption. In these cases, encryption is a must.
Reasons Why Encryption Matters
Why is encryption important? Here are three reasons
- Internet privacy concerns are real – Encryption helps protect privacy by turning personal information into “for your eyes only” messages intended only for the parties that need them — and no one else. You should make sure that your emails are being sent over an encrypted connection, or that you are encrypting each message. Most email clients come with the option for encryption in the settings menu, and if you check your email with a web browser, take a moment to ensure that SSL encryption is available.
- Hacking is big business – Hackers aren’t just bored kids in a basement anymore. They’re big business, and in some cases, they’re multinational outfits. Large-scale data breaches that you may have heard about in the news demonstrate that people are out to steal personal information to fill their pockets.
- Regulations demand it – Healthcare providers are required by the Health Insurance Portability and Accountability Act (HIPAA) to implement security features that protect patients’ sensitive health information. Institutions of higher learning must take similar steps under the Family Education Rights and Privacy Act (FERPA), while retailers must contend with the Fair Credit Practices Act (FCPA) and similar laws. Encryption helps businesses stay compliant as well as helps protect the valuable data of their customers.
Cryptographic hash functions
Encryption is usually a two-way function, meaning the same algorithm can be used to encrypt plaintext and to decrypt the ciphertext. A cryptographic hash function can be viewed as a type of one-way function for encryption, meaning the function output cannot easily be reversed to recover the original input. Hash functions are commonly used in many aspects of security to generate digital signatures and data integrity checks. They take an electronic file, message or block of data and generate a short digital fingerprint of the content called a message digest or hash value. The key properties of a secure cryptographic hash function are:
- Output length is small compared to the input
- Computation is fast and efficient for any input
- Any change to input affects lots of output bits
- One-way value — the input cannot be determined from the output
- Strong collision resistance — two different inputs can’t create the same output
The ciphers in hash functions are optimized for hashing: They use large keys and blocks, can efficiently change keys every block and have been designed and vetted for resistance to related-key attacks. General-purpose ciphers used for encryption tend to have different design goals. For example, the symmetric-key block cipher AES could also be used for generating hash values, but it’s key and block sizes make it nontrivial and inefficient.
Encrypting This Data is Achieved Mainly Through
- Full disk encryption (FDE) – the primary way to protect computer hard drives and the at-rest data on them. Any files saved to the disk (or an external hard drive) are automatically encrypted. There are intermediate options for disk encryption, as well–folder encryption, volume encryption, etc.–that aren’t quite full-disk encryption, but in between.
- File encryption – a way to encrypt at-rest data on a file-by-file basis so it cannot be read if intercepted. This isn’t automatic, but it’s beneficial because that data will stay encrypted after it’s left its place of origin.
- End-to-end (E2E) encryption – obscures any content of messages so only senders and receivers can read it, like the early Pretty Good Privacy (PGP) email encryption software. The idea with E2E encryption is that it tackles all the vulnerabilities on the communication chain: the middle (intercepting a message during delivery), and both ends (sender and receiver). This is not just a niche offering any more, either—platforms like Facebook Messenger and Apple’s iMessage have E2E encryption now, too.
- Encrypted web connections – via HTTPS, encrypted web connections use a Secure Sockets Layer (SSL) or transport layer security (TLS) protocols. With secure internet connections, we’re able to have better-protected communications on the web. These aren’t impenetrable, but there’s less risk of exploit. How it works: HTTPS uses SSL and TLS certificates when a browser and server communicate over the web. These are encryption keys, and when both browser and server have them, they’re authorized to access the encrypted data that’s passed between them. It’s a very basic, but very important, security measure when connecting to the web. If you’ve ever seen “https” instead of “HTTP,” or noticed a lock in the URL bar of your browser, you’re accessing a secure site.
- Encrypted email servers – S/MIME (Secure/Multipurpose Internet Mail Extensions) public key encryption essentially gives SMTP (simple mail transfer protocol) email servers a leg up by allowing them to send and receive encrypted messages, not just simple text messages.
- Pre-encrypting data that’s synced with the cloud – there’s plenty of software available that can pre-encrypt data before it even gets to the cloud, making it unreadable by the cloud or anyone who hacks into it. Note that any files still stored on the local machine aren’t encrypted and are still vulnerable. This accounts only for files sent to the cloud encrypting tech.
Encryption can be simple, like secret-key, or incredibly complex, like the Advanced Encryption Standard (AES), depending on the algorithm and the length of the key. The longer the key, the more protection, but also the more processing power required to handle the encrypting and decrypting process.
A Few Types of Encryption to Know Include
- Secret-key algorithms – Also known as symmetric algorithms, or private-key, this algorithm uses the same key for encryption and decryption. This is a touch more vulnerable because anyone who gets a hold of that one key can read anything you encrypt. Also, passing that secret key over the internet or network connections makes it more vulnerable to theft.
- Public-key algorithms – These are also known as asymmetric algorithms. With public-key encryption, there are two different, related encryption keys—one for encryption, and one for decryption. The public key is how the information is sent to you, and the private key decodes it (much like having a secure lock box on your front porch that a delivery person can put a package in, then only you can access that package with your private key). The benefit here is the key isn’t subject to being sent over insecure networks, but it does require more computer processing power so it’s a bit slower.
- Block ciphers – Like the Triple Data Encryption Standard (DES), or 3DES, these encrypted data a block at a time. Triple DES uses three keys and is a pretty great encryption option for financial institutions that need to protect sensitive information.
- Stream ciphers – A symmetric algorithm, it uses a keystream, a series of randomized numbers, to encrypt plaintext one character at a time. Rabbit, W7, and RC4 are popular stream ciphers.
- Elliptic curve cryptography – A form of public-key encryption, it can be practically unbreakable for normal computers, or “hard.” This is security industry speak for technology that’s not completely unbreakable but is generally accepted to be up to best standards.
- Blockchain cryptography – Blockchain technology is essentially a type of distributed database, best known as the basis for Bitcoin, that uses cryptography to safely store data about financial transactions. Blockchain cryptography is a form of “cryptocurrency,” using public-key encryption, and it’s valuable in its ability to provide direct, trustworthy and fraud-proof transactions between users on a peer-to-peer network. Because blockchain databases are distributed, they’re more resilient in the face of a DOS attack, so more companies are exploring this.
A Few Popular Algorithms Include
- Advanced Encryption Standard (AES) – A block cipher, this is pretty much the gold standard, per the U.S. Government. It offers 128-, 192-, and 256-bit encryption, the last two reserved for instances that require extra-strength protection.
- RSA – This asymmetric algorithm uses paired keys and is pretty standard for encrypting information sent over the internet, although it’s been through some issues of getting broken, which have then been resolved.
- IDEA (International Data Encryption Algorithm) – This block cipher with a 128-bit key has a great track record for not being broken.
- Signal Protocol – This open-source encryption protocol is used for asynchronous messaging, like email.
- Blowfish and Twofish – Both of these block ciphers are free to use and popular among e-commerce platforms for protecting payment information. They were created by the same person and offer symmetric encryption with keys varying in bit length. Twofish is the successor and offers longer encryption keys.
- Ring Learning With Errors or Ring-LWE – This protocol ramps up elliptic curves by adding in a new type of encryption that might be unbreakable by quantum computers.
What Is Key Management and Why Is It Important
Key management is another important aspect of encryption. Keys are how all of that encrypted data becomes readable, so how you handle them is just as sensitive as the data itself.
Many businesses worry about this aspect of encryption—after all, if you lose an encryption key, you lose access to your data, too. That’s why key management dictates how keys are stored (and shared) so prying eyes can’t get a hold of them, making your entire encryption schema moot.
- Diffie-Hellman key exchange – This secure way for people to create a key allows them to share secure information. This method is also touted as “perfect forward secrecy,” meaning that theoretically, at no point in the future can message encrypted with a Diffie-Hellman key be decrypted.
- Double Ratchet algorithm – Based on the above, the Double Ratchet algorithm is a key management algorithm used in end-to-end encryption of instant messaging, like the Signal messaging app.
This article just scratches the surface of the art and science of encryption, but hopefully, it gives you enough basic understanding of this important security technology. If you’re considering enlisting the help of a data security expert, you’re in luck: there are plenty of IT security freelancers on Upwork with expertise in encryption who are able to consult with you on an encryption strategy that’s best for you and your data



Visitor Rating: 5 Stars